Today’s Q&A was with Angela Mosino, an expert in cybersecurity and Executive Officer at Cyber Eye Global Strategies.
Before recording, Angela and Diane Dye, the CEO of People Risk Consulting, had a conversation about people risk and how its the biggest risk to cybersecurity.
Diane: All right, so the biggest risk to cybersecurity is the resistance or the know it all of your own people. Can you explain more?
Angela: So there’s a, there’s this knowledge piece and the understanding of the importance to follow the framework. And the most resistant are the business owners who don’t speak cyber and they speak business. And they speak business well, but they’re business owners who don’t have a cybersecurity background. And then the IT people, they’re not cybersecurity.
Diane: How do we tell the story of cybersecurity in a way where people are going to get it? And what kind of risk is cybersecurit coming into this new era right now, where it is the main front of attack? What are the statistics on that?
Angela: Cyber attacks are on the rise all over. But what they’re not talking about is a mid-sized company that has over 300% higher level for vulnerabilities and attacks. So, whether it be a large company or medium sized company the risk is high. Anything they say over 100 employees would be within that medium sized company and they, in general, are even at a higher risk than the large companies. But, here is how the larger companies get attacked. What happens is those small companies open a back door into those larger companies. So, even if the larger company thinks that they’ve implemented their controls and they’re pretty knowledgeable about cybersecurity, there are risks that are not accounted for.
Diane: How can companies protect themselves?
Angela: Larger companies do business with the smaller companies who lack cybersecurity knowledge and understanding. So risk professionals at learger companies need to look at their software, at those vulnerabilities, what they’re developing and implementing. How are they embedding in security into those processes every step of the way within an organization? Whether its in the HR department or in software product development, cybersecurity needs to be embroidered into the process.
Diane: Where does people risk come in?
Angela: People tend to silo themselves based upon what they know and what tasks they’re performing. So breaking down those silos is one of the hardest things to do. That’s why it’s important to advance the individual knowledge of every individual within an organization is key. So cybersecurity is going to be the modern day war. That’s where we’re heading. So people need to be educated on all fronts.
Diane: I have heard of cyber-attacks referred to as “modern day warfare.” Can you expand on what that means?
Angela: On a daily basis, I get anywhere between three to five intel reports of different types of attacks. So Microsoft has been hit heavily of recently. You know, we look at the risks and where we have the most to lose, obviously, our airplane industry, our healthcare industry. So what we need to do is and the biggest piece is, you’re correct, we talk to individuals about the risk. The risk is the individuals within your organization.
Diane: Have you had a case study where you have seen individuals, leaders in an organization go, oh, yeah, we need to. We need to do this?
Angela: When you look at it, what sells the most or convinces people the most is when you look at similar cybersecurity attacks, different cases that have happened, and you present those cases to them and say, “well, look, this is another company or this is a church that didn’t have cybersecurity.” Ultimately they thought it was a contractor sending them the email. They sent out the invoice for $800,000. And guess what? They lost their money. So once you start showing the case scenarios, what’s happening? That’s when people start to get on board.
If you’re catering to a small to mid-sized business, one cyber attack has the ability to close the doors within six months. That’s the average statistic. So that being said, when you look at cyber attacks, people subscribe to cyber insurance. Those rates are going up. The cyber insurance is not going to cover because you’ve not done due diligence, which requires you, or they’re now asking for you to implement those security pieces.
Diane: What has the potential to create the biggest wave of change in cybersecurity?
Angela: So I think if you had to ask me, what has created the biggest wave of change is education. Educate them on the cases, educate them on the types of attacks, and then turn around, give them simplistic ideas and things that they can implement from an individual standpoint and as a group standpoint.
Diane: What are the common things that you hear when there’s resistance to change?
Angela: Money. Money’s always the first one, right? Well, we can’t do that because we don’t have the funds to do that.
A lot of the changes that are required in cybersecurity, the number one area that you can improve in is what we call access control, meaning, have you locked your front door or not? I mean, it literally is that easy. So you think about it, that’s the use of multifactor authentication. You know, changing your passwords, password complexity, those sort of things. That doesn’t cost a lot of money to do. But so what they’re describing as why they can’t do it, in most cases, it’s not realistic. The reasoning, the resistance is there by lack of knowledge. So the way to reach them and to educate is by the knowledge.
These are the things you can do that are easy and implementable on an individual basis. These are the things from a group standpoint. And if you were looking at your business as a whole, this would be the pool and a prioritization based upon your return on investment. Right? So some people wouldn’t care about, because they don’t operate the technology to take credit card payments. But they use a third party vendor to do it. So they don’t care about PCI compliance. If you are a company that takes payment and that company got hacked and those people’s information gets lost, what does that do to your reputation? Because at the end of the day, your reputation means a lot, especially as a small to medium-sized business.
Diane: Reputation is a make or break thing. And a lot of companies come to People Risk Consulting because of reputation. Reviews are showing up on Indeed or Glass door that tell the story of employee experience. And they say, “oh, that’s just one. Disgruntled employee. That’s just one. That’s just one.” It’s not just one. You know, just like a cybersecurity breach is probably not just one employee who’s not in compliance.
Angela: How do you help leaders understand and embrace change?
Diane: What I’ll do to help stakeholders understand things is bring them through the lens of something called expectancy value theory. So an expectancy value theory (Feather, 1892), there’s a deep thing that these people expect to happen. I spend this money, this is what I expect to happen.
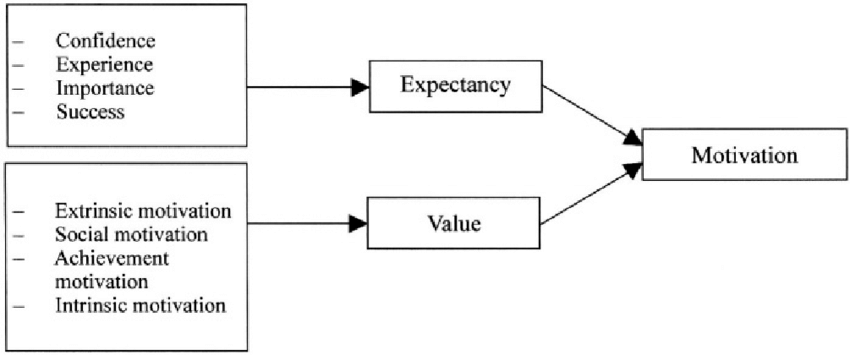
And there’s good expectancies and then there’s the bad expectancies. Like, “we just threw $500,000 down a deep, dark hole and nothing changed.” Or, “we wasted our money. We caught chicken little syndrome, the sky was falling and it didn’t,” whatever those expectancies are. And then there’s what they value. What they value might be sometimes in direct conflict with what they expect. So, if they value stability, that’s the doorway to cybersecurity education, understanding that value. And from that value, that’s where the motivation drives action. So having those deep conversations, pre-education, is important. It’s essential to get underneath those fears and uproot some of that stuff while at the same time leaning into the aspiration.
I think there’s a lot of people right now know the environment that we’re in right now. But it’s almost like “if I didn’t see it didn’t happen.” If a tree falls in the forest and no one’s there, it doesn’t matter. It’s not in my backyard right now, so I’m totally okay. And it seems to me, as a business educator, that the real conversation stems around, what are you afraid of by doing it?
Angela: That’s usually how we say it is. What keeps you from sleeping at night. And from executive level, it’s, you know, what, it’s reputational and, you know, closing the doors or the monetary.
Diane: So how do you explain it in a way that makes sense to leaders when cybersecurity might not be top of mind for them?
Angela: From a cyber perspective, we use the CIA triad. We use level of impact, meaning based upon the company, they. They evaluate their assets. That might be people, that might be computers, it might be product, service, whatever it is that they do.
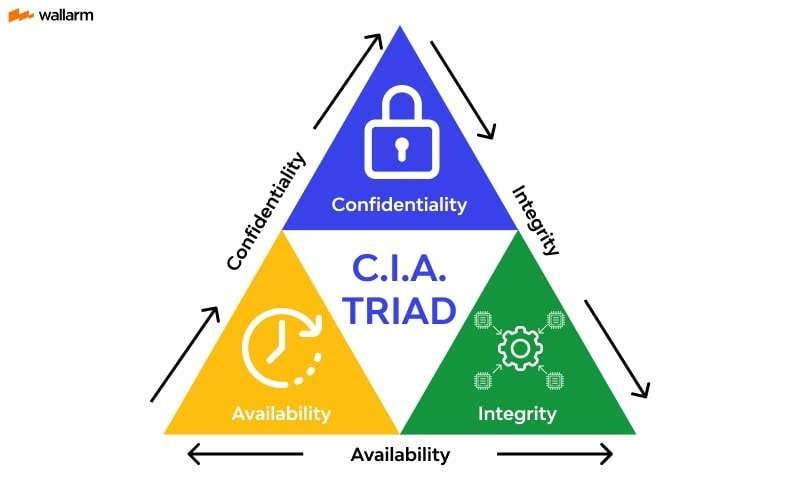
Based upon that CIA triad, which is availability, integrity, and confidentiality. So which ones of those are most important? And that’s how we develop a risk register as well. So based upon that risk register, we help them prioritize what is the highest level for them.
And then based upon the highest level, those are the things that we’re going to start with. First. We’re going to start with looking at their confidentiality, because confidentiality leads to all the legal considerations. Then, integrity. We’re looking at where data could be changed, and maybe they’re making payments for things that they shouldn’t. Or instead of $1,000 payment, they made a $10,000 payment. That leads to monetary consequences, right? And then availability tends to be the last one because it would be better that it’s not available if it’s not functioning well or if it’s not being protected.
Diane: In the people risk category, you also hold a lot of private employee data as a company. Hospitals hold patient data, HIPAA. There’s also regulatory privacy concerns.
Angela: Exactly. So in most cases, you’ll see that the first place that they’re going to be looking at is that confidentiality, if they have anything of value, you know, from an HR perspective, that should always be their first piece, right?
Diane: Yes! Social Security number leaks. I mean that’s the biggest hit, right? HR holds identifying information that can be used to steal your employees’ identitities. So you don’t have to be a big banking entity. Your mid sized business gets hit, all your employee data is yanked, and soon all of your employees Social Security numbers, everything, are on the dark web. What does that do to employee trust? How does that breach of trust impact performance? Retention?
Angela: Well, or think about it from something that’s not even banking. You look at a marketing company. A marketing company has its clients. Those clients make payments to you, right? You’ve got their names, you’ve got their addresses, you’ve got how much they paid, what their services were. If somebody was able to hack your repository of information in that data or your taxes or whatever that might be, I mean, look at the consequences of it, right? So that marketing agency, guess what, they’ve just been hacked and all of their clients have been spilled over onto the dark web. So there are many instances. I recently commented on an issue with Microsoft. Microsoft sells a product, expensive product, obviously, that’s where teams is driven and they’ve developed this platform with all the functionality on it.
Even on my personal email, I’m getting things from PayPal. I’ve got one from Apple, from the repair shop. I haven’t put anything in there, but guess what? If you happen to click that, what they do is it that gives them a way to get into your system and then they move laterally. A lot of these viruses have the ability to stay undisclosed for on average 18 months to 24 months. So what you think is clean may not be.
Diane: So they just lie and wait?
Angela: That’s right. And they’re, at the same time, guess what they’re doing? They’re learning all your passwords because they’ve got that back end access. Right. They’re also learning what times are the high times, what’s the network traffic look like? They’re learning all your patterns. And then when they go in to make that move, they’re going to make the most catastrophic move they can, or they’re going to use it to have pulled your data to ask for ransomware. So something that seems small, I see about 10,000 phishing attempts a month and we get hundreds of attachments that are on those, which is like, you know, a big one of the bigger nos and a much quicker way to get in. That being said, we still have about 150 individuals within the company that end up doing it. We train consistently, we require continuous training.
We teach about cybersecurity. We have a phishing button, but that does not prevent it. And what happens is people get busy, they’re not rationalizing it, they’re not really thinking about it. And that’s where at the end of the day, that human factor will always be your biggest vulnerability.
Diane: And it’s a factor that like, no algorithms can really predict it with accuracy. There, there aren’t predictive analytics for human behavior that are accurate because you can’t say when someone’s going to be too busy and accidentally click on something.
Angela: Right? Well, I mean, so imagine somebody’s had a really hard weekend. They come in, they’re tired, they haven’t slept much, they’ve had a situation, a mom or dad has been sick, whatever. Are you going to be thinking as clearly as maybe at other points? So just something as basic as that.
Believe it or not, even working in cyber and working with people that are of cyber minded, we still have incidences where they click occasionally and, you know, we have what we call a B2B. Essentially, it’s a service that you can subscribe to that continuously tests and assesses the level of cyber savviness of your people. And that’s a common, you know, subscription you can subscribe to. You can kind of add different things to it. Over the holidays, they tend to add more of the gift cards and promotions and bonuses sort of scenarios to it. But at the end of the day, you’d be surprised who clicks it.
Diane: So that would be very interesting to do. A feature on is who actually ends up clicking on some of these things. I think where your company and my company have a great place in the sandbox together is that education piece, that understanding piece from that executive side about the people risk associated with non adoption of these things and the reputation, the money loss, the risk of closure, the loss of trust. I mean, that is huge. The loss of trust in an organization ripples all the way down. I may, I’m a big believer in creating environments that drive disclosure and driving the voice behavior that recognizes risks in an organization. Organizations win when they recognize failures and don’t make them a punitive thing. They make them an, okay, we need to back this up and we need to learn from this.
That disclosure piece matters to psychological safety in an organization which immediately connects to the ability to comply with cybersecurity, to accept cybersecurity measures, to say something without embarrassment. If you clicked on something that, I mean, that’s massive. The fear, the unnecessary fear of being punished for being human is damaging.
I think you had a brilliant idea. It’s like, yeah, let’s send out something and say, look who actually clicks on it. Not have it be anything that’s malicious or malware or phishing, but have it be something that would model that. Do a click, study on that, and then advertise that to normalize the fact that it happens to everyone. And if you do it within the organization, you’re not going to get in trouble for a mouse click.
You’re not going to lose your job for a mouse click. I think one of the biggest problems in your cybersecurity battle, Angela, is the fact that organizations don’t have these environments of disclosure and they’re not disclosure prepared. So they, someone says something, they don’t know what to do. Like someone just said something, I don’t know what to do. So then what that creates is that hush. Just don’t, just don’t say anything. And that’s so dangerous. The hush culture that can crop up in organizations is so damaging to psychological safety, physical safety, financial safety, reputation. You know, all of these things, it’s incredibly damaging. And I think until organizations realize exactly how damaging, they’re going to continue to get hurt.
Connect with PRC to learn how you can develop a disclosure preparedness plan for your company.




